Disabling HTTPS redirection for Citrix VDI in a Box web access.

Update: 22/08/2012 For VDI in a Box 5.1
One of my dislikes for VDI in a Box is the SSL redirection that takes place as soon as you attempt to log in to the web access portal.
SSL redirection I can live with, but the self signed certificate in VDI in a box can’t even be trusted and added as a known host due to the spaces in the name.
So, if you are doing a proof of concept and like me, can’t be arsed fighting with certificate import on these devices, here’s a quick tip to flat out turn off the SSL redirection for desktop logins.
Fire up winscp, and log into the VDI in a box appliance.
Navigate to /home/kvm/kvm/install/servlet_container/webapps/dt/web-inf
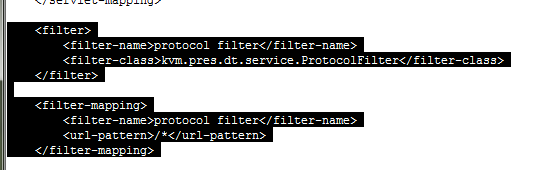
take a copy of the web.xml (you’ll thank me if you balls this up)
edit the Web.xml file and remove the highlighted section below:
Save the file
Putty / SSH to the device and issue a “tc_start” to restart tomcat
Note: For VDI in a Box 5.1, I’ve found early copies of the appliance didnt contain this command. If tc_start is not available, reboot the virtual machine via the console or web gui.

Now browse to the http address, tada! No more silly ssl errors.

NOTE: the admin console will still redirect, if you wish to disable this too, remove the following if statement from /home/kvm/install/serlet_container/webapps/admin/index.jsp





For those that do want to use an SSL certificate at zero cost, have a look at cacert.org. You’ll just need to import the root certificate into your web browser – not a big deal for testing purposes.
Thanks, got that going for our test setup, now if there was a way to get rid of the ssl requirement for the Citrix Receiver setup for testing ( but enabled for production)
Thanks for the advice. But to clarify this modification, will this simply disable the internal https redirection for ViaB or will this also disable the external redirection as well that is published via CAG?
Hi ken,
This should only disable the internal traffic, the access gateway will still tunnel via ssh.
That being said, I haven’t tested it, do backup the file before hand.
This did not work. I can now get to the vdi site by using http:// however I cannot log on with any users; it tells me my credentials are invalid. The receiver will not connect either.
I restored the web.xml file back to its default state and now cannot connet to any desktops.
I’ve done this fix twice, just to make sure I wasn’t crazy and have gotten the same results.
The only option is to have a CA issue you a certificate.
Hi Joel,
Very sorry it didn’t work for you, it’s worked a number of times for me in my lab without issue.
If you would prefer to take this offline my email address is on the about page above.
I would make sure you do the command tc_start afterwards for the change to take effect.
Thanks!
For some strange reason tc_start wasn’t present in the pre release, but yes it’s definitely there now.
I’ll amend the article.
A
Andrew, is the procedure the same for ViaB 5.0.2? I have one client that is still running this version and not 5.1.
Thanks.
Ken
Hi ken,
Should be fine, just backup the file before changes.
A